Most compliance teams discover wallet segregation the hard way.
They start with a simple setup: one hot wallet for operations, maybe a cold wallet for reserves. It works until their first compliance audit. Or their first tainted inbound transfer. Or their first regulator asking how they prove customer funds never touched DeFi.
Then begins a rebuild that follows a remarkably consistent pattern. Teams in Singapore, London, São Paulo, and New York all arrive at nearly identical architectures. Not because they copied each other. Because the underlying constraints force convergence.
This post documents that pattern. If you're building stablecoin infrastructure in 2026, you're going to end up here eventually. Might as well understand why.
What Is Wallet Segregation and Why Does Compliance Require It?
Wallet segregation means maintaining separate blockchain addresses for distinct operational purposes, with controlled flows between them.
This is not optional complexity. It solves three specific risks that regulators and auditors care about:
Risk 1: Arbitrary inbound transfers: Anyone can send stablecoins to any public address. This includes mixers, hacked funds, and sanctioned entities. If your customer operations wallet receives tainted USDC, you need a way to isolate that flow without contaminating your entire balance.
Risk 2: Protocol exposure: If you deploy capital to DeFi protocols for yield, those protocols pool funds from thousands of unknown counterparties. Regulators want proof that your customer funds never touched those pools.
Risk 3: Fund provenance: When a customer withdraws, the transaction shows up on a blockchain explorer. If it shows their funds came directly from an Aave lending pool, that creates uncomfortable questions. If it shows funds came from your known operational wallet, that is clean provenance.
Wallet segregation solves all three by creating buffer layers between external exposure and customer operations.
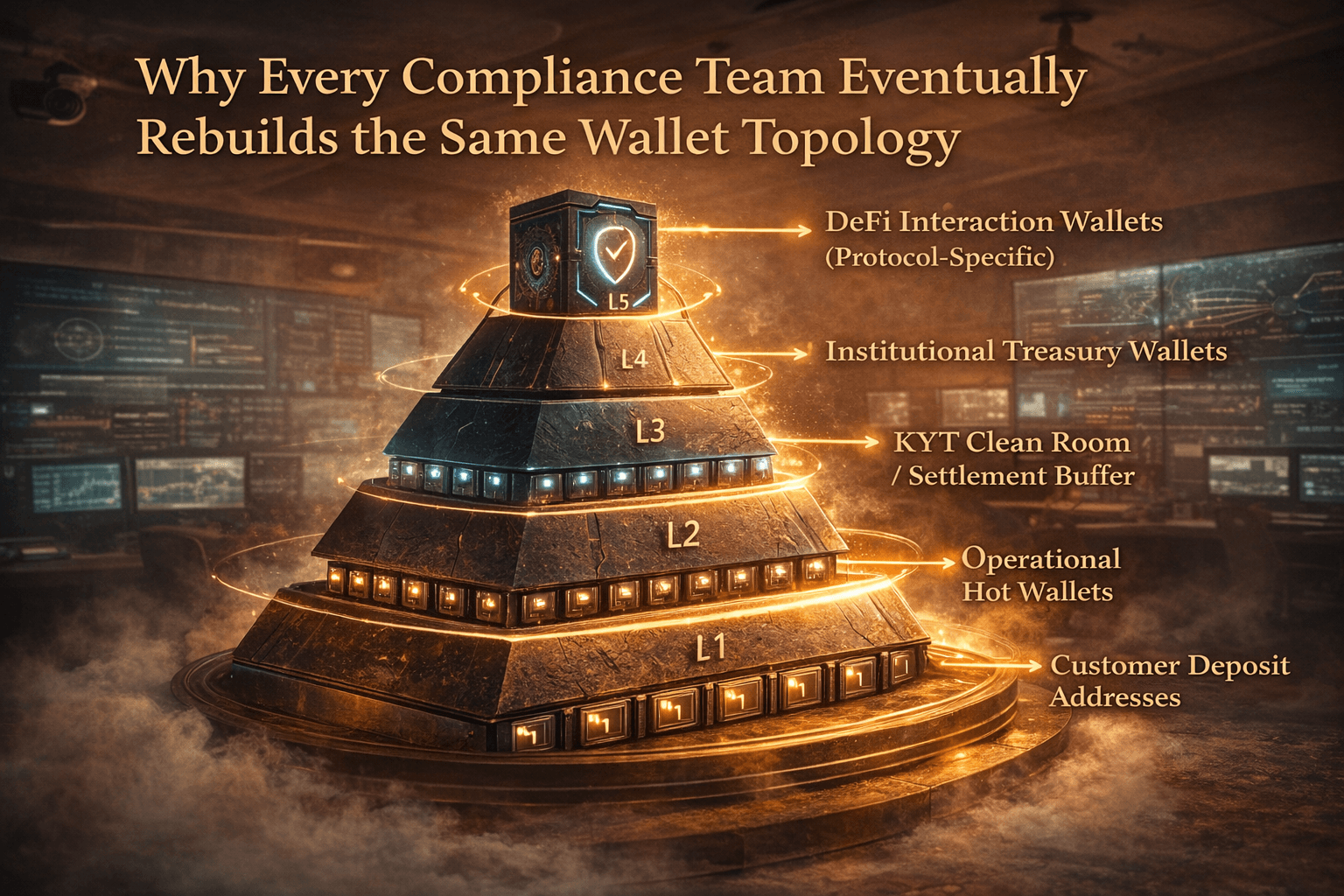
The Five-Layer Architecture Everyone Converges On
After watching dozens of compliance teams go through this evolution, a canonical architecture has emerged. The layers are:
Layer 1: Customer Deposit Addresses
One address per customer or per deposit. These are public-facing and will receive both clean and potentially tainted flows. Every inbound transfer gets screened by KYT (Know Your Transaction) tools. These addresses never interact with DeFi.
Layer 2: Operational Hot Wallets
Sweeps deposits from Layer 1. Consolidates balances. Applies first-pass KYT screening. Still not authorized to touch DeFi protocols.
Layer 3: Settlement Buffer (The Clean Room)
This is the first ring-fenced environment. It only receives funds from internal operations or approved custody. All inbound is KYT-verified before funds can move outbound. Think of it as an airlock.
Layer 4: Institutional Treasury Wallets
Holds institution-owned funds only. 100% provenance-clean capital. Never receives external inbound. This is the entry point for DeFi deployment. Only funds that have passed through Layers 1-3 ever reach here.
Layer 5: Protocol-Specific DeFi Wallets
One wallet per protocol (Aave, Morpho, Kamino, etc.). Outbound only to protocol contracts and back to Layer 4. Inbound only from protocol contracts and Layer 4. Never interacts with customers. Never receives random external transfers.
The critical design principle: each layer has one purpose. Funds flow unidirectionally through the stack, with KYT gates between each transition.
How KYT Gates Work Between Layers
KYT screening happens at every layer transition, not just at deposit time. This is where most early-stage implementations get it wrong.
The flow from customer deposit to treasury looks like this:
Customer deposits USDC to their Layer 1 address
KYT immediately scans the inbound transaction
Sweep to Layer 2 operational wallet (screened again)
Move to Layer 3 clean room (must pass KYT to proceed)
Internal accounting tags funds as "clean capital"
Move to Layer 4 treasury (verified clean, now eligible for DeFi)
If any KYT check fails, the flow routes to a quarantine wallet. The flagged transaction is isolated. The original address is not marked as permanently tainted.
This distinction matters: KYT evaluates individual transaction flows, not addresses. One bad inbound does not contaminate an entire wallet. Only that specific flow gets flagged. This is how major institutions handle dusting attacks.
Why Taint Tracking Is Transaction-Level, Not Address-Level
This is one of the most misunderstood aspects of compliance architecture.
Many teams initially assume that if a tainted transfer lands in a wallet, the entire wallet is compromised. This would make operations impossible on public blockchains, where anyone can force-send tokens to any address.
The actual compliance standard works differently:
Taint follows specific transaction paths: source to destination
An address that receives unsolicited tainted funds is not itself tainted
The institution is responsible for what it moves forward
Moving tainted funds onward creates liability. Receiving them does not.
When a tainted inbound arrives, correct handling looks like:
KYT triggers automatic alert
Only the inbound flow is marked high-risk
Funds immediately route to quarantine wallet
The original address remains clean for future operations
Manual review determines disposition of quarantined funds
Regulators understand this model. Institutions cannot prevent unsolicited inbound. They can control what they do next.
Why DeFi Interactions Do Not Contaminate Withdrawals
A common concern: if treasury funds go into a DeFi pool with unknown counterparties, how can customer withdrawals be clean?
The answer is architectural. Properly designed systems never route directly from DeFi to customer.
What institutions never do:
Layer 5 DeFi Wallet → Layer 1 Customer Withdrawal
What institutions actually do:
Layer 5 DeFi → Layer 4 Treasury → Layer 3 Clean Room → Layer 2 Ops → Layer 1 Customer
By the time funds reach the customer withdrawal address, they have been:
Verified clean by KYT at multiple transitions
Passed through institutional wallets
Stripped of direct DeFi provenance
The customer sees "Payment from [Institution] operational wallet" on the block explorer. Not "Payment from Aave lending pool."
KYT providers classify DeFi protocol interactions as "protocol interaction: low risk" rather than "received funds from unknown third party." The protocol is infrastructure, not a counterparty.
The Four Compliance Principles That Drive This Architecture
Four regulatory principles explain why this architecture keeps emerging:
Principle 1: KYT evaluates flows, not addresses: Taint follows specific transactions. An address is not permanently compromised by one bad inbound.
Principle 2: DeFi protocols are not counterparties: Analytics engines distinguish between receiving funds from a person versus interacting with a smart contract. Protocol interactions carry different risk weight.
Principle 3: Institutions control what they move: Receiving unsolicited funds creates no liability. Moving those funds forward does. This is why quarantine exists.
Principle 4: Multi-layer transfers break taint chains: An external observer tracking funds sees a chain of institutional wallets. The DeFi exposure happens entirely within treasury operations, invisible to the customer flow.
When Do Teams Realize They Need This Architecture?
The pattern is consistent. Teams rebuild their wallet structure after one of these triggers:
After the first compliance audit: Auditors ask: "Show me the flow from customer deposit to customer withdrawal." If it passes through a DeFi protocol, they ask: "How do you prove customer funds were not exposed to unknown counterparties?" No good answer means a finding.
After the first exchange freeze: A customer complains that Coinbase or Kraken flagged their deposit from your platform. Investigation reveals your payout wallet has mixed provenance from DeFi interactions. Now every customer withdrawal triggers enhanced review at destination exchanges.
After the first regulatory inquiry: A regulator asks about fund segregation. You explain that customer deposits and treasury operations share the same wallet. The conversation does not go well.
After reaching material scale: At $1M in daily volume, simple setups work. At $50M, the operational risk of not having segregation becomes existential. One tainted transaction can freeze your primary operational wallet.
Most teams rebuild proactively after the audit. Some wait for the exchange freeze. A few wait for the regulatory inquiry. No one waits twice.
The Build vs. Buy Decision
Every team faces the same question: build this architecture internally or use infrastructure that implements it?
Building internally requires:
Smart contract or wallet management expertise
KYT provider integrations at every layer
Quarantine workflow automation
Multi-signature governance for layer transitions
Ongoing maintenance as regulations evolve
3-6 months for initial implementation, assuming experienced team
Arguments for building:
Full control over architecture
No dependency on external vendors
Custom rules for specific use cases
Arguments for using infrastructure:
Faster deployment (weeks vs. months)
KYT integrations pre-built
Architecture already audited
Maintenance handled by vendor
Cost amortized across customers
Infrastructure providers like RebelFi have productized this architecture. Their Midas platform implements the five-layer model with KYT gates between transitions, automatic quarantine routing, and protocol-specific DeFi wallets. This approach treats ring-fencing as turnkey infrastructure rather than custom development.
The decision often comes down to core competency. If your business is building financial applications, wallet architecture is probably not where you want to differentiate. If your business is custody or infrastructure, you may want full control.
What This Architecture Does Not Solve
Wallet segregation with KYT gates solves fund provenance and regulatory audit requirements. It does not solve:
Smart contract risk: If a DeFi protocol gets exploited, funds in Layer 5 are at risk regardless of wallet architecture.
Yield volatility: Segregation does not affect what returns you earn on deployed capital.
Regulatory uncertainty: This architecture reflects current best practices. Regulations will evolve.
Operational complexity: More layers means more transactions, more gas costs, more systems to monitor. This is a tradeoff, not a free lunch.
The architecture is defensive infrastructure. It protects against compliance and provenance risks. Other risks require other solutions.
How to Evaluate Your Current Architecture
If you operate stablecoin infrastructure, these questions reveal architectural gaps:
Can you show auditors the complete flow from any customer deposit to any customer withdrawal, with KYT verification at each step?
If a tainted transfer arrives at one of your wallets tomorrow, does that wallet get frozen, or just that specific transaction?
Do your customer-facing wallets ever interact directly with DeFi protocols?
Can you prove that customer funds never touch pools with unknown counterparties?
When a customer withdraws, does the blockchain show your operational wallet as the source, or a DeFi protocol address?
If any answer reveals a gap, you are somewhere on the path to the five-layer architecture. The question is whether you arrive there proactively or after an incident.
The Pattern Recognition Summary
Compliance teams rebuild wallet infrastructure because constraints force convergence:
Public blockchains allow arbitrary inbound transfers
Regulators require fund segregation and audit trails
DeFi yield requires protocol exposure
Customers need clean provenance on withdrawals
KYT screening must happen at every transition, not just deposit
The five-layer architecture with KYT gates is not clever design. It is the minimum viable structure that satisfies all constraints simultaneously.
Teams arrive here through different paths. Some after audits. Some after incidents. Some proactively after learning from others' experiences. But they arrive at the same place because the problem is the same everywhere.
If you are building stablecoin operations infrastructure in 2026, you will build some version of this. The only variable is whether you build it before or after you need it.